You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
Copy file name to clipboardExpand all lines: packages/@aws-cdk/aws-pipes-alpha/README.md
+34-12
Original file line number
Diff line number
Diff line change
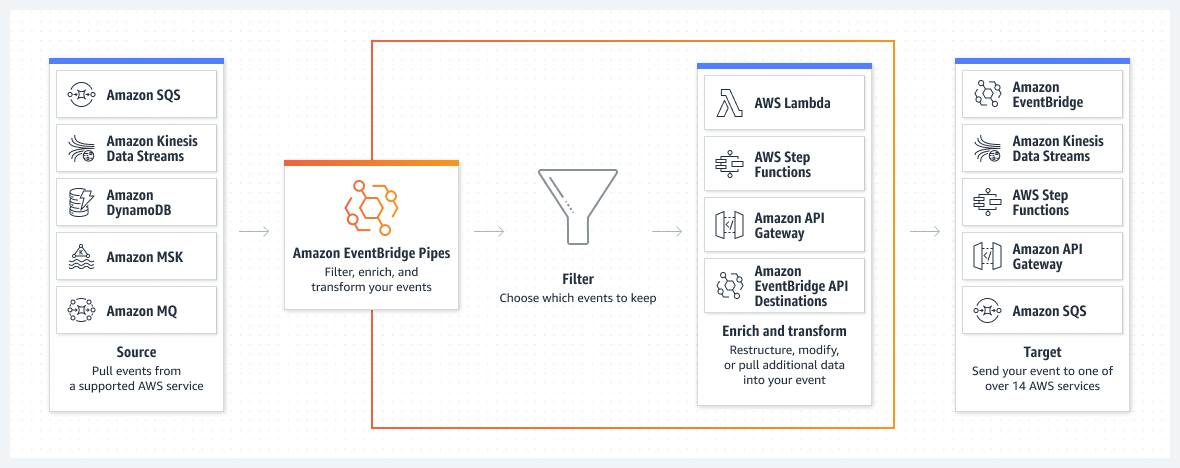
@@ -23,7 +23,7 @@ can be filtered, transformed and enriched.
23
23
24
24
25
25
26
-
For more details see the [service documentation](https://docs.aws.amazon.com/eventbridge/latest/userguide/eb-pipes.html).
26
+
For more details see the [service documentation](https://docs.aws.amazon.com/eventbridge/latest/userguide/eb-pipes.html).
27
27
28
28
## Pipe
29
29
@@ -65,7 +65,7 @@ A source is a AWS Service that is polled. The following sources are possible:
This example shows a filter that only forwards events with the `customerType` B2B or B2C from the source messages. Messages that are not matching the filter are not forwarded to the enrichment or target step.
109
109
110
-
You can define multiple filter pattern which are combined with a logical `OR`.
110
+
You can define multiple filter pattern which are combined with a logical `OR`.
111
111
112
112
Additional filter pattern and details can be found in the EventBridge pipes [docs](https://docs.aws.amazon.com/eventbridge/latest/userguide/eb-pipes-event-filtering.html).
113
113
@@ -117,7 +117,7 @@ For enrichments and targets the input event can be transformed. The transformati
117
117
A transformation has access to the input event as well to some context information of the pipe itself like the name of the pipe.
118
118
See [docs](https://docs.aws.amazon.com/eventbridge/latest/userguide/eb-pipes-input-transformation.html) for details.
119
119
120
-
### Example - input transformation from object
120
+
### Example - input transformation from object
121
121
122
122
The input transformation can be created from an object. The object can contain static values, dynamic values or pipe variables.
123
123
@@ -185,7 +185,7 @@ If the transformation is applied to a target it might be converted to a string r
185
185
186
186
In cases where you want to forward only a part of the event to the target you can use the transformation event path.
187
187
188
-
> This only works for targets because the enrichment needs to have a valid json as input.
188
+
> This only works for targets because the enrichment needs to have a valid json as input.
Copy file name to clipboardExpand all lines: packages/@aws-cdk/aws-pipes-alpha/test/integ.pipe-kmskey.js.snapshot/PipesKmsKeyTestDefaultTestDeployAssert1065A2A1.assets.json
0 commit comments