-
Notifications
You must be signed in to change notification settings - Fork 1.6k
[Auth] Fixed macOS extension keychain access by adding recommended kS… #9102
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Auth] Fixed macOS extension keychain access by adding recommended kS… #9102
Conversation
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thanks a lot for the investigation and contribution @kamilpowalowski! I've approved the CI workflows.
Have you completed the Google CLA?
|
@ncooke3 No problem :) I need that for my own app so I was motivated. Yes, I completed Google CLA yesterday. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
LGTM. I added one request below. Thanks again @kamilpowalowski!
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thank you for the contribution! One minor comment, and there's a new merge conflict in the changelog that needs to be resolved before merging this, but otherwise LGTM!
…ecUseDataProtectionKeychain key
…g to separated function.
|
@kamilpowalowski do you have an idea by any chance if this would also fix a similar bug on tvOS? |
|
@nidegen, I don’t think so. It fixes a behavior related strictly to macOS. On macOS, you have access to the whole keychain. On other systems, you shouldn't have that problems. But (if possible) you should try to set |
#9102) * [Auth] Fixed macOS extension keychain access by adding recommended kSecUseDataProtectionKeychain key * Refactored FIRAuthStoredUserManager to extract keychain query building to separated function.
Fixes #8950, #6876
I'm working on the app that used Firebase Auth for authentication. I have an iOS app with iOS Share Extension and macOS app with macOS Share Extension.
By adding Keychain Access Group, I can use authenticated accounts between the main iOS app and iOS Share Extension. But the same code doesn't work on macOS.
When the app is installed on macOS or when I'm trying to access it from macOS Share Extension, I always get a prompt to keychain access. I started to dig, and I found the keychain parameter https://developer.apple.com/documentation/security/ksecusedataprotectionkeychain
from its documentation, we can find
It can be added to all platforms:
kSecUseDataProtectionKeychainkey is also mentioned in https://developer.apple.com/documentation/security/ksecattraccessgroup documentationBut I have to limit it a bit with
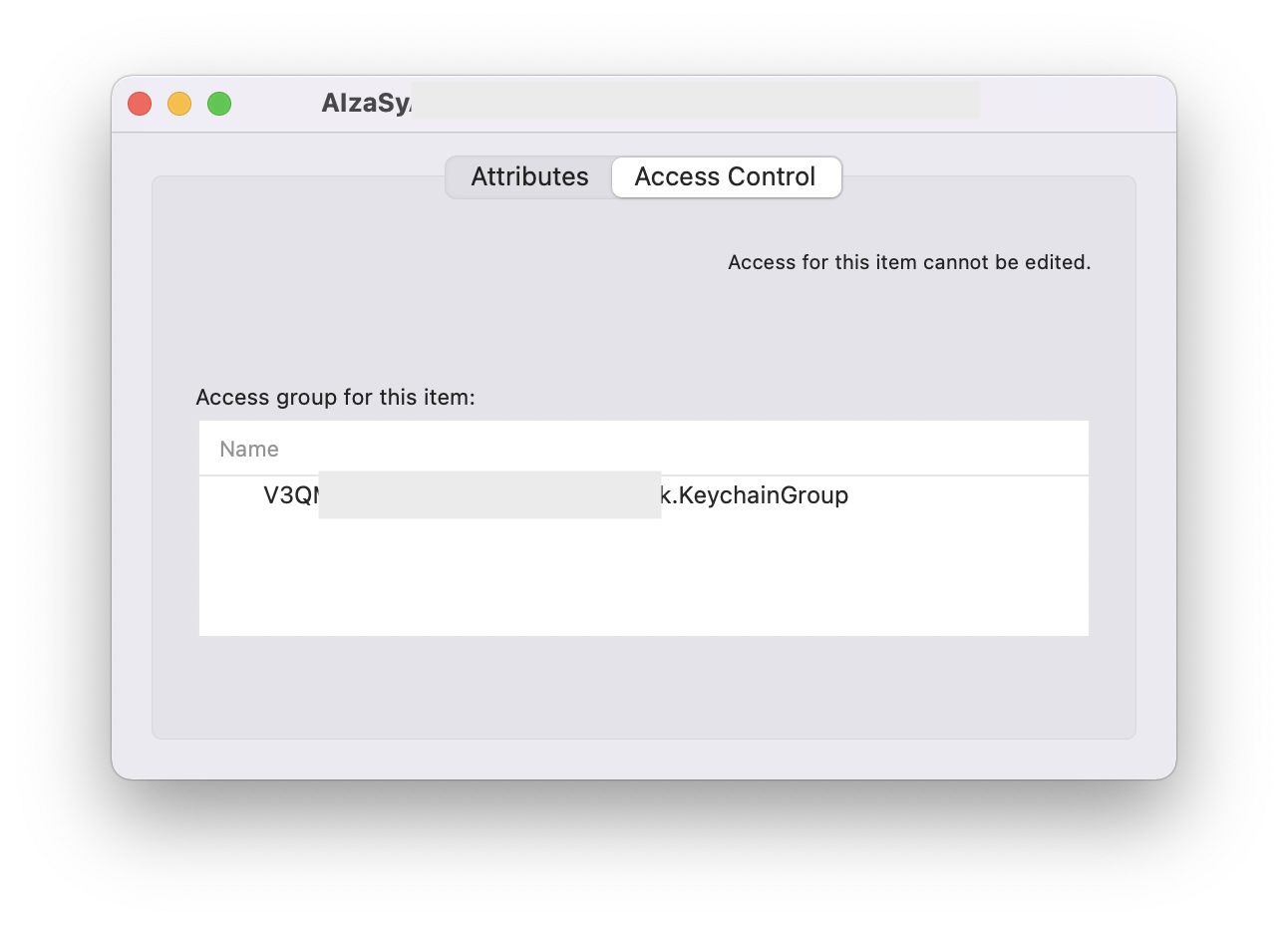
@availableparameter.I took screenshot from keychain without that key (only main app listed)

and a screenshot from keychain after key added (KeychainGroup access instead is listed)